MITM attack. Man in the middle cyberattack, active eavesdropping example and unprivate online communication vector Illustration Stock Vector Image & Art - Alamy

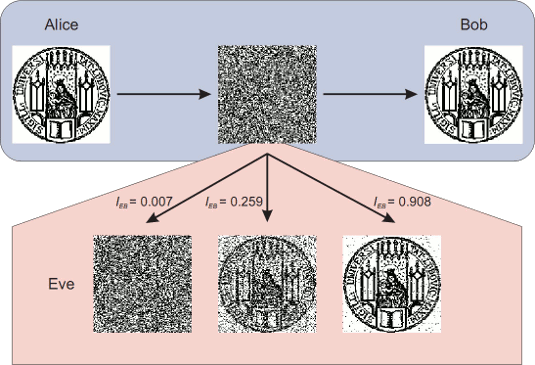
Electronics | Free Full-Text | Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory for Massive MIMO-Enabled IoT

Analysis and Validation of Active Eavesdropping Attacks in Passive FHSS RFID Systems | Semantic Scholar

PDF) Defending Against Randomly Located Eavesdroppers by Establishing a Protecting Region | Octavia Dobre - Academia.edu
![PDF] Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory for Massive MIMO-Enabled IoT | Semantic Scholar PDF] Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory for Massive MIMO-Enabled IoT | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6eaeb5847b258c8a1cfa351d3723ee49c0407531/3-Figure1-1.png)
PDF] Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory for Massive MIMO-Enabled IoT | Semantic Scholar

Tech vansh - What is an Eavesdropping Attack? #ethicalhacking #hacking #kalilinux #cybersecurity #hackers #hack #hacker #linux #python #anonymous #technology #programming #security #infosec #ethicalhacker #developer #malware #pentesting #web #hacked ...
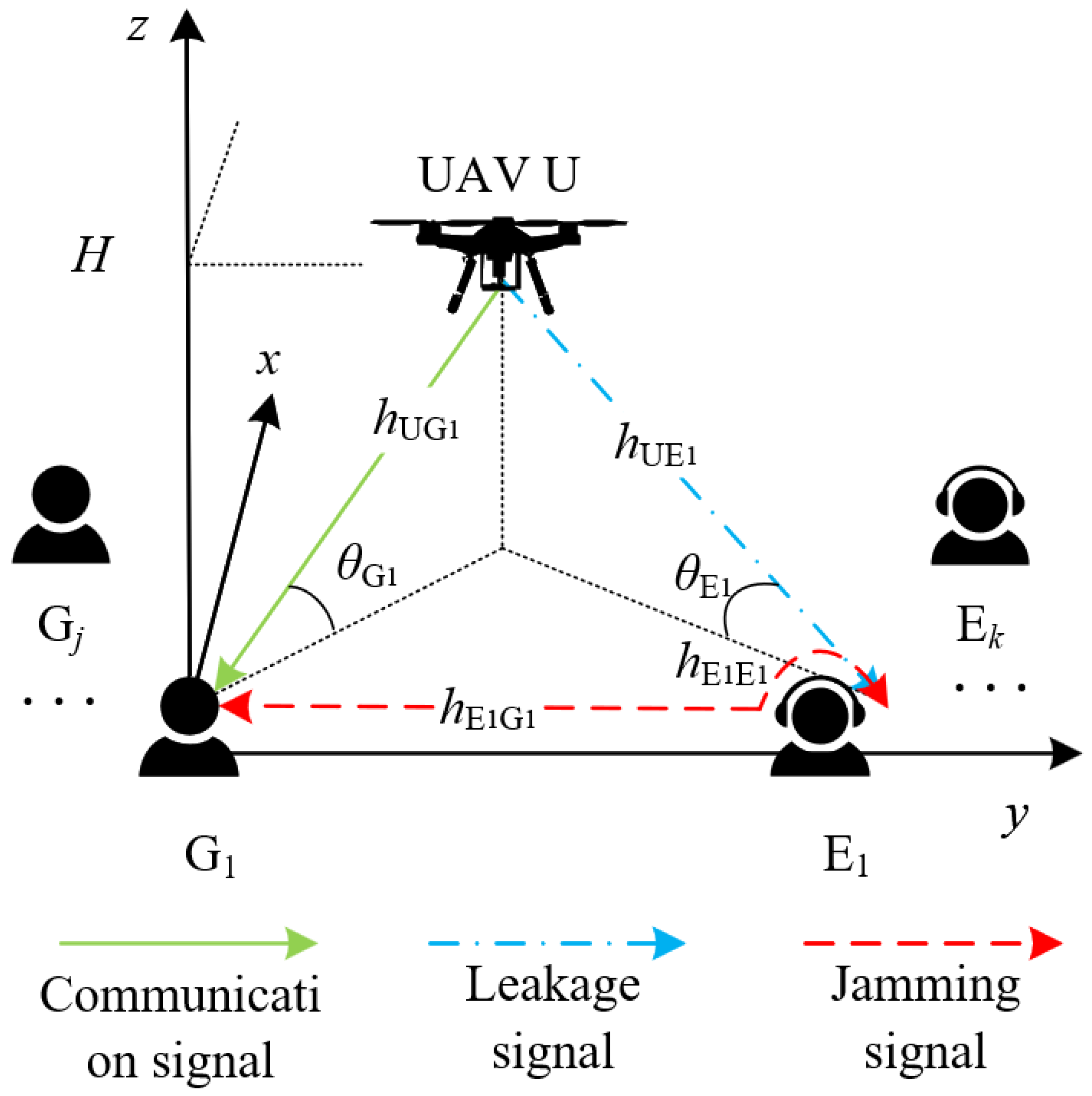
Drones | Free Full-Text | Safeguarding UAV Networks against Active Eavesdropping: An Elevation Angle-Distance Trade-Off for Secrecy Enhancement

An illustration of active eavesdropping in massive MIMO-based systems. | Download Scientific Diagram

On Eavesdropping Attacks in Wireless Sensor Networks with Directional Antennas - Hong-Ning Dai, Qiu Wang, Dong Li, Raymond Chi-Wing Wong, 2013







![PDF] Eavesdropping Attacks on High-Frequency RFID Tokens | Semantic Scholar PDF] Eavesdropping Attacks on High-Frequency RFID Tokens | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d62c281dffed526cf12937c4b320a2b74226ae05/5-Figure1-1.png)