FKM NBR Silicon Seal Rings O Ring PU Mpu CPU Parts with Varisized Shape Rubber Parts - China O Ring, Seal Ring | Made-in-China.com

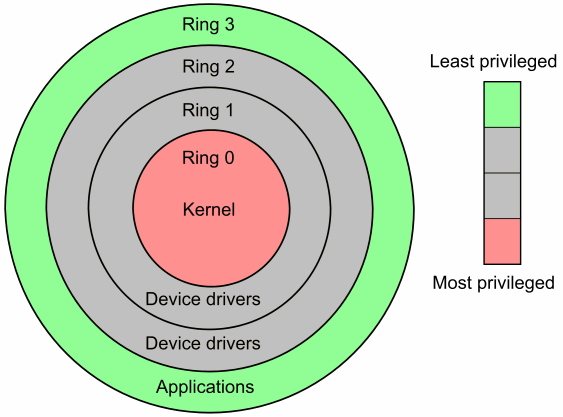
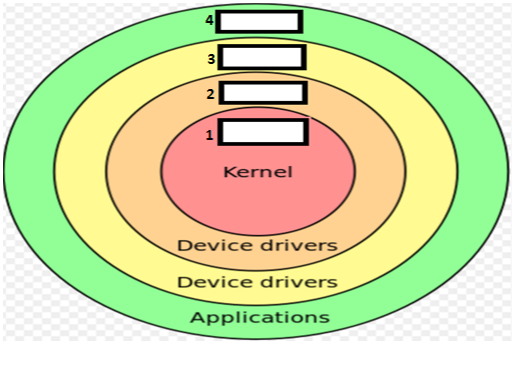
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
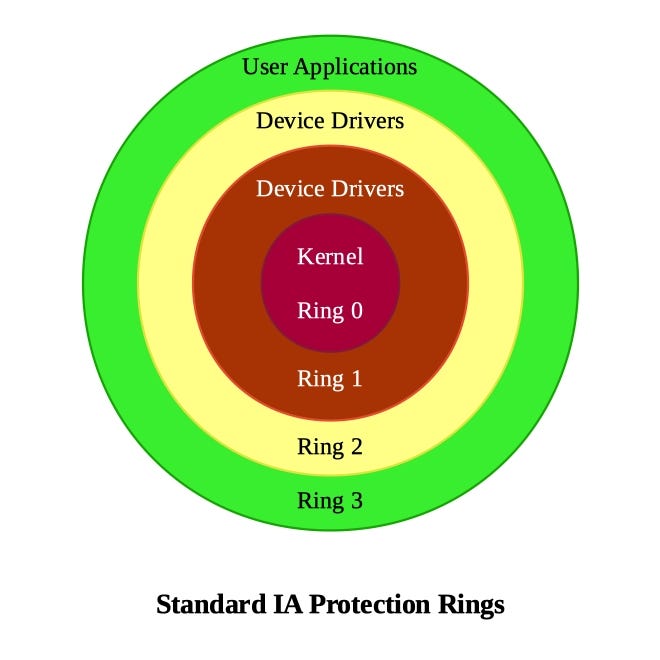
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium

A descriptor ring containing 8 elements. Descriptors 1 to 4 belong to... | Download Scientific Diagram
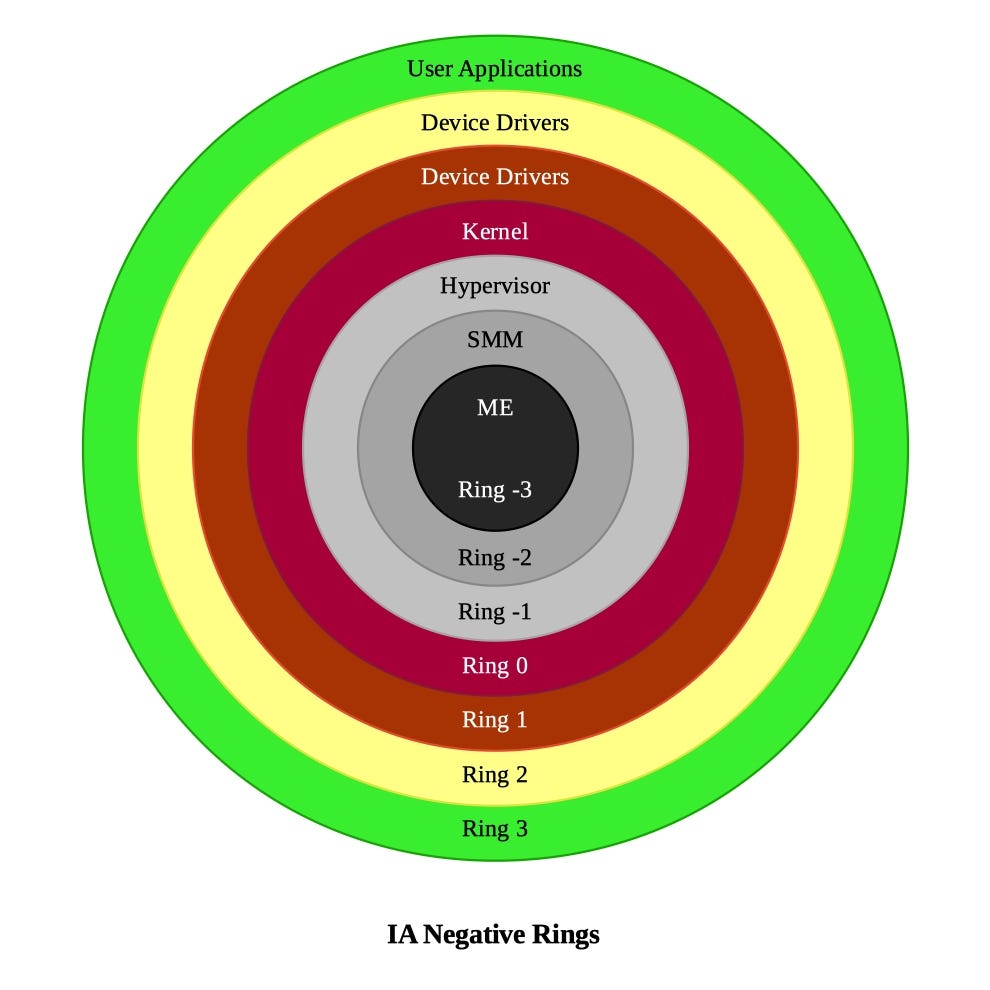
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
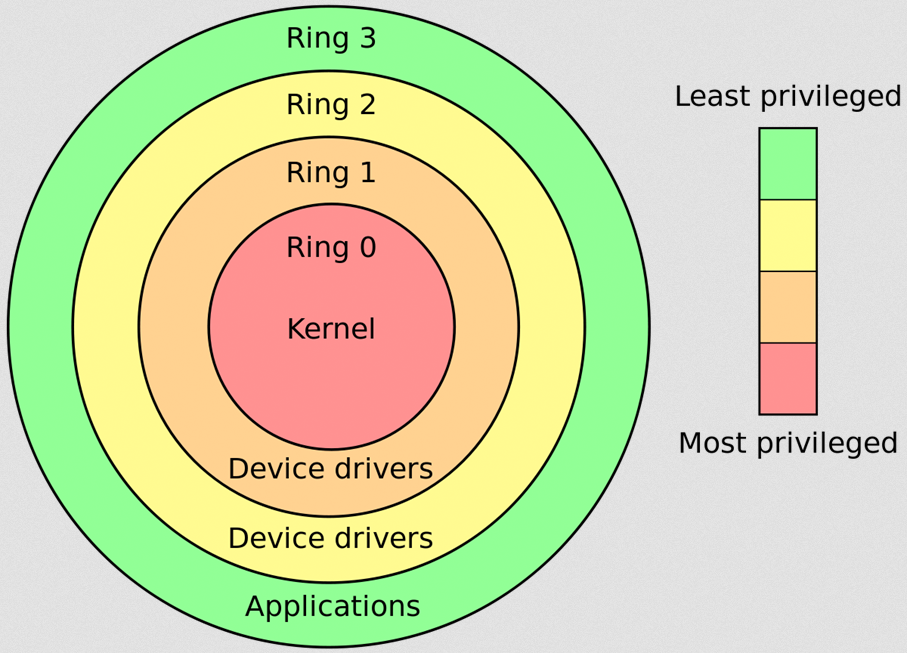
CPU Protection Ring | Stronghold Cyber Security | NIST 800, CMMC, IT RISK ASSESMENTS | 1-888-277-8320

operating system - What is the difference between the kernel space and the user space? - Stack Overflow

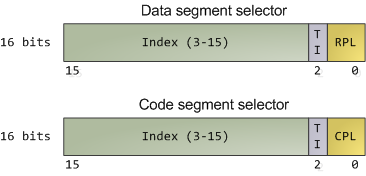


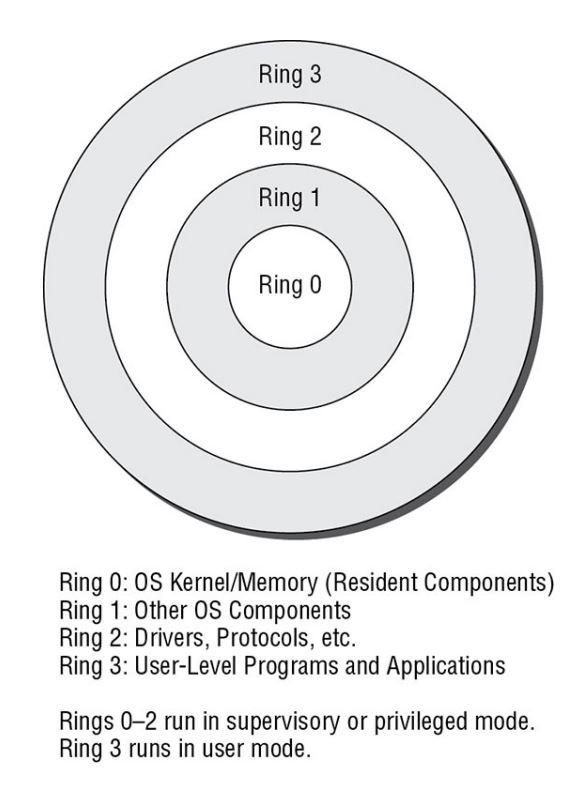
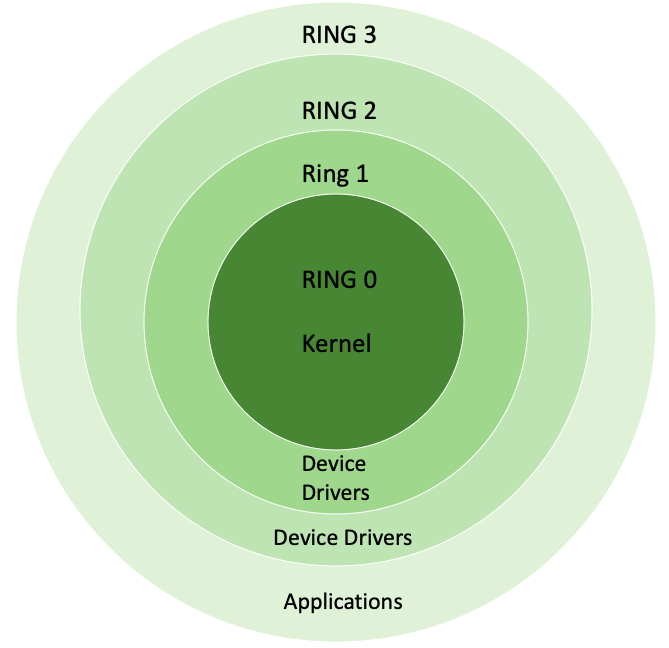


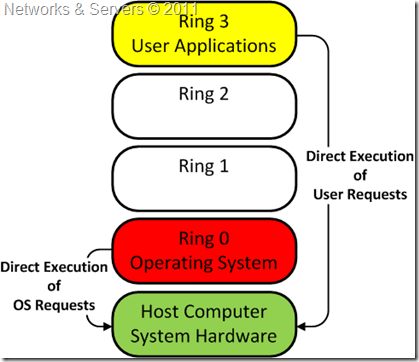
![Privilege levels or rings on the x86 - Hands-On System Programming with Linux [Book] Privilege levels or rings on the x86 - Hands-On System Programming with Linux [Book]](https://www.oreilly.com/api/v2/epubs/9781788998475/files/assets/d2294bba-9ac8-444b-9ed8-18f3223ddc66.png)